Here you will find answers to Drag and Drop Questions – Part 2
Question 1
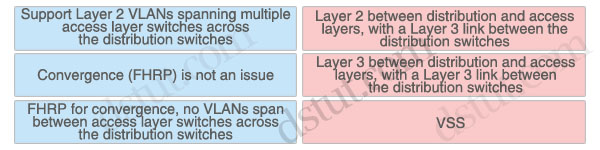
Drag the network characteristic on the left to the design method on the right which will best ensure redundancy at the building distribution layer
Answer:
Layer 2 between distribution and access layers, with a Layer 3 link between the distribution switches:
FHRP for convergence, no VLANs span between access layer switches across the distribution switches
FHRP for convergence, no VLANs span between access layer switches across the distribution switches
Layer 3 between distribution and access layers, with a Layer 3 link between the distribution switches:
Support Layer 2 VLANs spanning multiple access layer switches across the distribution switches
Support Layer 2 VLANs spanning multiple access layer switches across the distribution switches
VSS: Convergence (FHRP) is not an issue
Question 2
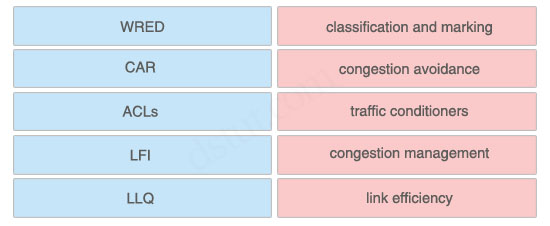
Click and drag the QoS feature type on the left to the category of QoS mechanism on the right.
Answer:
+ classification and marking: ACLs
+ congestion avoidance: WRED
+ traffic conditioners: CAR
+ congestion management: LLQ
+ link efficiency: LFI
+ congestion avoidance: WRED
+ traffic conditioners: CAR
+ congestion management: LLQ
+ link efficiency: LFI
Explanation
Classification is the process of partitioning traffic into multiple priority levels or classes of service. Information in the frame or packet header is inspected, and the frame’s priority is determined.Marking is the process of changing the priority or class of service (CoS) setting within a frame or packet to indicate its classification. Classification is usually performed with access control lists (ACL), QoS class maps, or route maps, using various match criteria.
Congestion-avoidance techniques monitor network traffic loads so that congestion can be anticipated and avoided before it becomes problematic. Congestion-avoidance techniques allow packets from streams identified as being eligible for early discard (those with lower priority) to be dropped when the queue is getting full. Congestion avoidance techniques provide preferential treatment for high priority traffic under congestion situations while maximizing network throughput and capacity utilization and minimizing packet loss and delay.
Weighted random early detection (WRED) is the Cisco implementation of the random early detection (RED) mechanism. WRED extends RED by using the IP Precedence bits in the IP packet header to determine which traffic should be dropped; the drop-selection process is weighted by the IP precedence.
Traffic conditioner consists of policing and shaping. Policing either discards the packet or modifies some aspect of it, such as its IP Precedence or CoS bits, when the policing agent determines that the packet meets a given criterion. In comparison, traffic shaping attempts to adjust the transmission rate of packets that match a certain criterion. Shaper typically delays excess traffic by using a buffer or queuing mechanism to hold packets and shape the ?ow when the source’s data rate is higher than expected. For example, generic traffic shaping uses a weighted fair queue to delay packets to shape the flow. Traffic conditioner is also referred to asCommitted Access Rate (CAR).
Congestion management includes two separate processes: queuing, which separates traffic into various queues or buffers, and scheduling, which decides from which queue traffic is to be sent next. There are two types of queues: the hardware queue (also called the transmit queue or TxQ) and software queues. Software queues schedule packets into the hardware queue based on the QoS requirements and include the following types: weighted fair queuing (WFQ), priority queuing (PQ), custom queuing (CQ), class-based WFQ (CBWFQ), and low latency queuing (LLQ).
LLQ is also known as Priority Queuing–Class-Based Weighted Fair Queuing (PQ-CBWFQ). LLQ provides a single priority but it’s preferred for VoIP networks because it can also configure guaranteed bandwidth for different classes of traffic queue. For example, all voice call traffic would be assigned to the priority queue, VoIP signaling and video would be assigned to a traffic class, FTP traffic would be assigned to a low-priority traffic class, and all other traffic would
be assigned to a regular class.
be assigned to a regular class.
Link efficiency techniques, including link fragmentation and interleaving (LFI) and compression. LFI prevents small voice packets from being queued behind large data packets, which could lead to unacceptable delays on low-speed links. With LFI, the voice gateway fragments large packets into smaller equal-sized frames and interleaves them with small voice packets so that a voice packet does not have to wait until the entire large data packet is sent. LFI reduces and ensures a more predictable voice delay.
(Reference: Cisco Press Designing for Cisco Internetwork Solutions)
Question 3
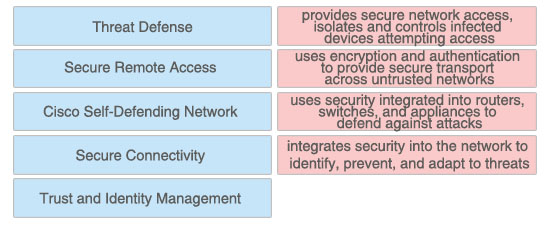
Click and drag the Cisco Self-Defending Network term on the left to the SDN description on the right. Not all terms will be used.
Answer:
+ provides secure network access, isolates and controls infected devices attempting access: Trust and Identity Management
+ uses encryption and authentication to provide secure transport across untrusted networks: Secure Connectivity
+ uses security integrated into routers, switches, and appliances to defend against attacks: Threat Defense
+ integrates security into the network to identify, prevent, and adapt to threats: Cisco Self-Defending Network
+ uses encryption and authentication to provide secure transport across untrusted networks: Secure Connectivity
+ uses security integrated into routers, switches, and appliances to defend against attacks: Threat Defense
+ integrates security into the network to identify, prevent, and adapt to threats: Cisco Self-Defending Network
Explanation
Trust and identity management solutions provide secure network access and admission at any point in the network and isolate and control infected or unpatched devices that attempt to access the network. If you are trusted, you are granted access.
We can understand “trust” is the security policy applied on two or more network entities and allows them to communicate or not in a specific circumstance. “Identity” is the “who” of a trust relationship.
The main purpose of Secure Connectivity is to protect the integrity and privacy of the information and it is mostly done by encryption and authentication. The purpose of encryption is to guarantee confidentiality; only authorized entities can encrypt and decrypt data. Authentication is used to establish the subject’s identity. For example, the users are required to provide username and password to access a resource…
Question 4
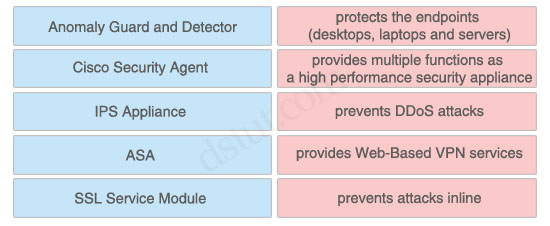
Match the Cisco security solution on the left to its function on the right.
Answer:
+ protects the endpoints (desktops, laptops and servers): Cisco Security Agent
+ provides multiple functions as a high performance security appliance: ASA
+ prevents DDoS attacks: Anomaly Guard and Detector
+ provides Web-Based VPN services: SSL Service Module
+ prevents attacks inline: IPS Appliance
+ provides multiple functions as a high performance security appliance: ASA
+ prevents DDoS attacks: Anomaly Guard and Detector
+ provides Web-Based VPN services: SSL Service Module
+ prevents attacks inline: IPS Appliance
Question 5
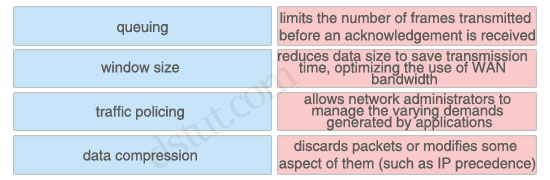
Answer:
limits the number of frames transmitted before an acknowledgement is received: window size
reduces data size to save transmission time, optimizing the use of WAN bandwidth: data compression
allows network administrators to manage the varying demands generated by applications: queuing
discards packets or modifies some aspect of them (such as IP precedence): traffic policing
reduces data size to save transmission time, optimizing the use of WAN bandwidth: data compression
allows network administrators to manage the varying demands generated by applications: queuing
discards packets or modifies some aspect of them (such as IP precedence): traffic policing
Question 6
Place the PPDIOO Methodology in the correct order
| Optimize | Step 1 |
| Design | Step 2 |
| Prepare | Step 3 |
| Implement | Step 4 |
| Operate | Step 5 |
| Plan | Step 6 |
Answer:
Step 1: Prepare
Step 2: Plan
Step 3: Design
Step 4: Implement
Step 5: Operate
Step 6: Optimize
Step 2: Plan
Step 3: Design
Step 4: Implement
Step 5: Operate
Step 6: Optimize
Question 7
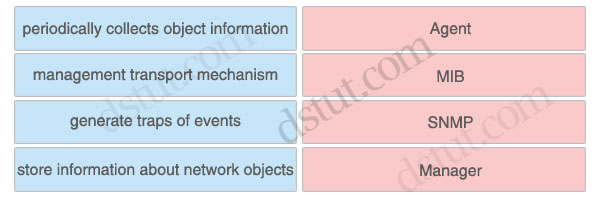
Answer:
Agent: generate traps of events
MIB: store information about network objects
SNMP: management transport mechanism
Manager: periodically collects object information
MIB: store information about network objects
SNMP: management transport mechanism
Manager: periodically collects object information
Explanation
The SNMP system consists of three parts: SNMP manager, SNMP agent, and MIB.
The agent is the network management software that resides in the managed device. The agent gathers the information and puts it in SNMP format. It responds to the manager’s request for information and also generates traps.
A Management Information Base (MIB) is a collection of information that is stored on the local agent of the managed device. MIBs are databases of objects organized in a tree-like structure, with each branch containing similar objects

No comments:
Post a Comment